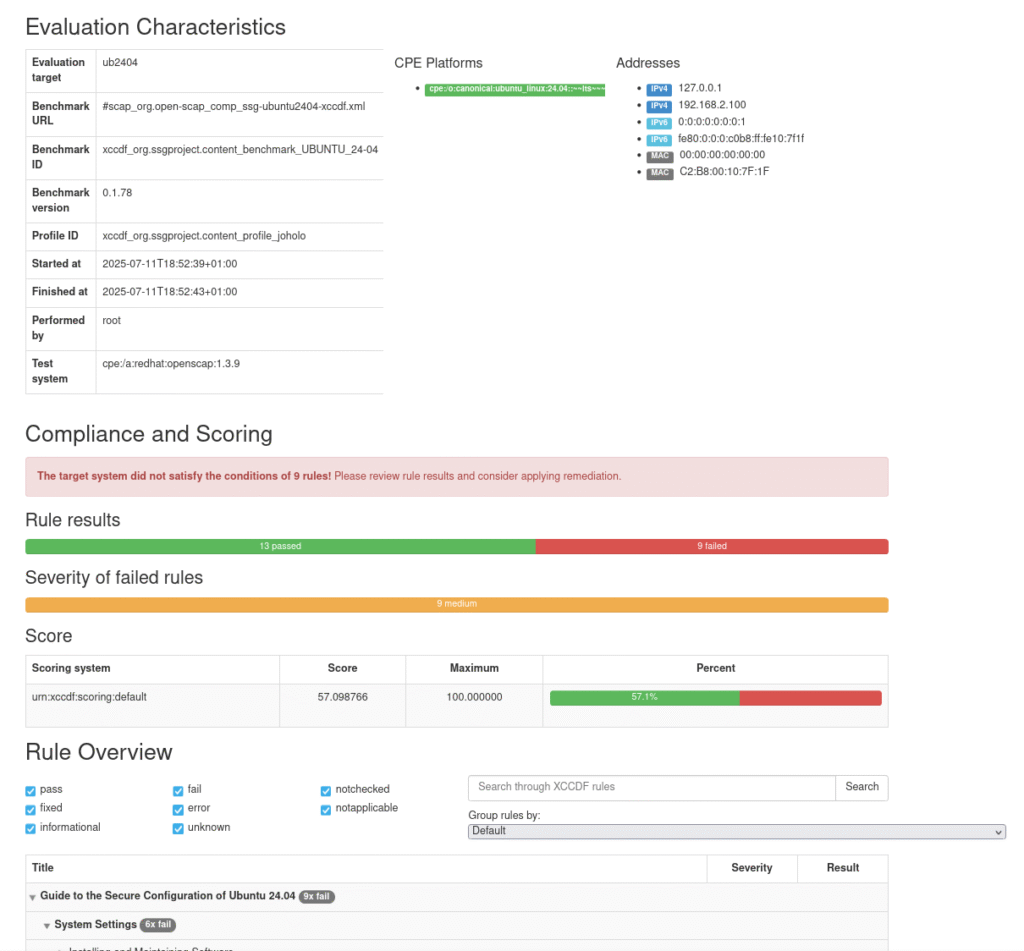
France just had their fourth Prime Minister in two years removed after losing a vote of no confidence. President Macron states that he will appoint a new one within a few days. That seems pointless. To lose one Prime Minister to a vote of no confidence means you don’t have the backing of the legislative assembly and it’s no good bashing your head against that wall hoping that somehow you will find yourself wielding a majority.
First a recap if you haven’t followed this: President Macron called for early parliamentary elections in 2023 because the EU-elections had shown that the electorate had substantially different allegiances than what was represented in the French parliament. The election lead to the current deadlock where no one commands a majority. Macron was blamed for this but I think he did the right thing. There was ample evidence that the electorate had changed their allegiances and the actual election bore this out. That a parliamentary deadlock resulted is the choice that the electorate made.
I think a reasonable critique of president Macron is that he should also have called for earlier presidential elections when the parliamentary vote showed that his group of supporting parties no longer commanded a majority. He did not do that. This seems inconsistent. Why first honour the spirit of the law(well, the constitution technically) in calling for early parliamentary elections if you then go on to hold high the letter of the law when there is equal evidence that the electorate no longer support the current president?
But this just crystallises the issues seen growing throughout Europe over the last twenty years: deadlock. Belgium, Northern Ireland, Sweden and France are just the first examples that spring to mind. In the case of Belgium they had no elected government for more than 500 days. In Northern Ireland they had a technocrat government for years, ostensibly because one party didn’t like the post-Brexit arrangement but in reality it was quite convenient for all parties to let non-politicians make a bunch of difficult decisions. In Sweden we didn’t have an actual work stoppage, merely the formation of unstable governments that struggled to maintain coherency.
It is my argument that this is bad. Technocrat governments are all well and good as a fallback mechanism but it is hardly beneficial if the government doesn’t represent what the electorate voted for, even when the way in which a deadlock was reached was through elections. If nothing else a government needs to be able to respond to emergencies. If someone hijacks a plane and there is disruption in air traffic and a bunch of other countries worried about their citizens being caught up in the situation, you are just making a fool of yourself saying “We have no one to make hard choices or balance different viewpoints for three weeks, please come back later”.
A long-term solution
How might we avoid deadlocks like these? Italy has an almost nuclear option where the largest party in the election results are given a bonus of extra seats in parliament. I don’t like this because it’s not proportional representation, where one vote equates to one equal part in the electoral process. Whoever voted for the party that got the most votes has their vote amplified to 120%, making all other voters demoted to only having 80% the influence(no, the arithmetic is more complicated than that, this was just a crude approximation). Not all countries have proportional representation, most notably the US and the UK. They have a first-past-the-post system so only by receiving the most votes in a constituency do you get any representation. So in the UK the Greens might have support from 10% of the population but only get 5% of the seats in parliament.
This “Italian” solution can also suffer from factions in a single party causing deadlocks. We shouldn’t assume that only deadlocks between parties can cause issues. So I suggest the following constitutional setup:
- A Caretaker government is formally recognized as being one that has been appointed by the legislative assembly but no longer commands a majority in that assembly(typically because they lose a vote of no confidence or because a parliamentary election is held).
- A Caretaker government can introduce new laws without parliamentary support unless the head of state blocks them(we need some checks and balances).
- A Caretaker government can be replaced as soon as the legislative assembly – through a majority vote – appoints a new government.
In the French case the government that ran the country before snap parliamentary elections were held would have stayed in power and would have been able to rule by decree. The French parliament would not have been asked to approve any reforms or budgets the government proposed. The government would just have all these things take effect without parliamentary approval. This seems very undemocratic but it is only slightly undemocratic. It’s still a government elected by the legislative assembly which in turn is a representation of what the electorate wants, just running past the most recent election and not requiring parliamentary approval for changes.
But this is not meant to remain the case for more than a few days or at most a few weeks before a new parliamentary majority is formed and a new government is appointed. But as is the case in France today, the old government would still be in charge since no parliamentary majority currently exists, two years after the most recent elections. The government themselves could say “We don’t think we have the proper mandate to run the country but there are three blocks in parliament refusing to agree on a new government so find ourselves still in power whether we like it or not…”
And this to me seems like a good sword of Damocles to hang over the various factions: agree on a new government or explain to the electorate why you have left the previous government in charge all this time. So the whole Caretaker government scheme is mostly meant as a big stick with which to pound parliament to at least agree on a government, but also serves as a workable plan B just in case the parliament is completely unwilling to… do things. Because as noted earlier, a country needs a government in place at all times, not just when parliament happens to see it fit to appoint one.
Complications
A Caretaker government would be expected not to diverge significantly from what the electorate seem to want at that point in time, even if that is quite different to what the government in question was elected to do some years back. This then becomes a little bit of a concern for whatever government is appointed by parliament, they may have to enact policies quite different to what they have themselves espoused if they find themselves lacking parliamentary backing. This can’t realistically be codified into the constitution and would only be an expectation, not a formal requirement. France demonstrates this quite well by the electorate voting in favour of various mutually exclusive factions, none of whom command a parliamentary majority. What even would a Caretaker government be expected to pursue? Making decisions that are unpopular in parliament can be both formally and operationally necessary.
The head of state would have the right to veto anything proposed by a Caretaker government. In France this would be the President but in Sweden it would be the King, which isn’t really viable for domestic political reasons. So the head of state isn’t necessarily the right person to wield veto powers over a Caretaker government. In Sweden the Supreme Court seems acceptable, because this is just to keep an outgoing government from abusing their last two days in office by outlawing all other political parties or passing a budget where no taxes are collected or something similarly malicious. In the former case the reform would have been struck down legally anyway, but this way it doesn’t even rise to the level of being seriously considered.
I have made it sound like once parliament agrees on a new government, all is well and we have continuity of government, but that is not the case. It would be perfectly feasible for the French parliament to appoint a government that no faction particularly likes but is deemed acceptable, only to then let the government achieve nothing. It’s not against the rules to vote against every single proposal put forward by a government you gave your support in parliament. This leads us to some awkward considerations.
One solution is to say that budgetary proposals have a special voting procedure. In the first round it works like today, you need a majority of all votes in parliament. The second round sees the smallest party ignored, all their votes are automatically set as “Abstains”. You keep going like this until only two parties remain. Now, this isn’t guaranteed to lead to a budget as the two largest parties could both vote “No” in this final round. However, I would argue that is the same as saying that the government has lost its parliamentary support and become a Caretaker government which can pass budgets without parliamentary approval. So a new budget still goes on to become binding.
Parliament could in that situation agree to create a new government just to get rid of the Caretaker government but to constantly go back and forth between party A and party B agreeing on a government only to later that same day agree on a vote of no confidence against the very same government makes these parties look pretty silly. Defining what constitutes a “budgetary proposals” is harder than it might seem. It’s trivially true when a formal budget is put forward but what about a separate legal instrument that requires enough funding to raise taxes by 1%? Either taxes are raised or existing expenditure is reduced to accomodate that change. Almost everything has some impact on state finances and the budget that was passed would really need to change to truly reflect what income and what expense is predicted*.
Another solution could be to mandate that parliament must have a budget in place by some date and if they fail to do that the president can put one in place covering the next period(usually a year). This raises similar questions as in the previous solution. What if parliament votes a law into force that prevents the Treasury from funding defence or health-care or whatever the parliament opposes at that particular point? In both solutions it makes sense to put in place a constitutional ban against any legal instrument that defunds, restricts or in some other way hinders the budget from being implemented. That’s precisely the sort of line in the sand that is going to be something that the supreme court has to define. Parliament will vote for a law, someone will say it undermines the established budget and the court has to rule on the subject. It can’t be exhaustively defined ahead of time.
Note that I’m not suggesting that we rule illegal everything that in some way hampers the implementation of the budget. There are a great many things that can’t keep a state from successfully implementing a budget, ranging from lower than projected tax receipts, investors not buying the state’s bonds and so on. You only look foolish if you declare them illegal. Zimbabwe for instance outlawed inflation when printing huge amounts of currency turned out to not improve the lives of the people of that country. It didn’t yield the results the government had promised, needless to say. But keeping parliament from interfering with the established budget is a reasonable restriction.
A short term solution
In most countries constitutional changes like the ones I propose above take time. In Sweden there must be two parliamentary votes separated by at least one general election to make a consitutional amendment. So in France they can’t really solve their current problem through constitutional changes. But Macron’s party Renaissance(RE) and it’s supporters can emulate this in a sense. Them voting against a vote of no confidence would be right and proper in the first case but when the second vote of no confidence was called they should all have abstained, basically saying “Since the government we appointed lost a vote of no confidence, we lay down our votes in any vote of no confidence in this parliament.”
That would have made it sensible for Macron to appoint a left-wing government that would receive backing from a majority of parliament – now with the centrist-Macron block bowing out. Rassemblement National(RN) would have thrown a hissy fit and accused RE of electing a left-wing government, but they would probably just say “No, the French people decided on that in the most recent election. We’re not voting for or against anyone at this stage and if this new government loses a vote of no confidence we urge the left-wing block to lay down their votes in future.”
This is a pretty harsh solution to attempt and some considerations should be taken into account. This would largely burn RE’s bridges with RN for the foreseeable future. Even if this forces RN to support Macron’s government it would be a short-term gain. RE and its supporters I think should play a different game and accept that they got thrown out of power by the French people. Burn your political mandate on the pyre of continuity of government and accept that this will make your vote-share go even lower, trusting your political opponents to make you look good in comparison as time goes by. Your popularity has to get worse before it can get better. It need not necessarily get better, but your only chance right now goes by heading down hill first.
A socialist government
So would a socialist government be good for France? I think it would be better than the current deadlock, but the I don’t think the socialist block will end up serving the French people well. I think a centrist and right-wing alliance would be better. But that’s not my call to make, that’s the decision of the French electorate. I don’t even have incontrovertible evidence of the socialist block’s impending failure, the rising cost of servicing France’s sovereign debt or the decreasing living standards that would ensue. If we had some Oracle-machine that showed us what the right answer was we would be on Easy street and could dispense with elections, but we don’t. So we just ask the electorate what they support and go with that, knowing full well that it might be the best route forward or it might end up harming the electorate well-being.
* A budget is not just a decision on what funds to allocate, it is a prediction of what income and expenses will be. The Region of Västra Götaland typically spend more than budgeted, which makes their budgets quite useless. There are statutory requirements of what certain branches of regional government must do and claiming year after year that you only allocate 90% of the money necessary to not violate the law is just silly. A person running a hospital won’t withhold medical treatment to save money because the budget said so, lest they find themselves facing criminal charges. A budget isn’t an instrument by which to achieve savings. Achieving savings can be entirely reasonable but a budget is not the instrument to do it. Statutory requirements for instance can only really be affected by turning to the legislative assembly which made the law in the first place.